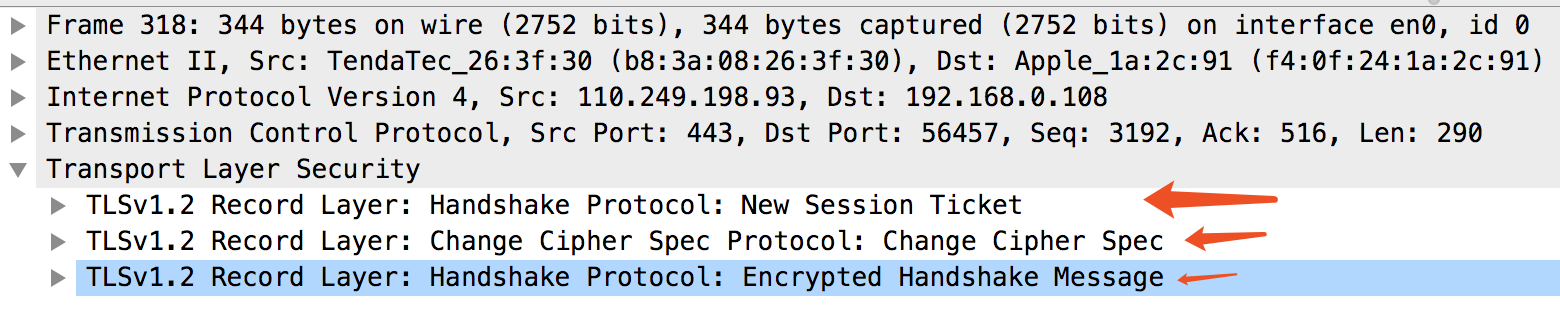
TLS/SSL协议结构
TLS/SSL协议位于应用层和传输层TCP协议之间。
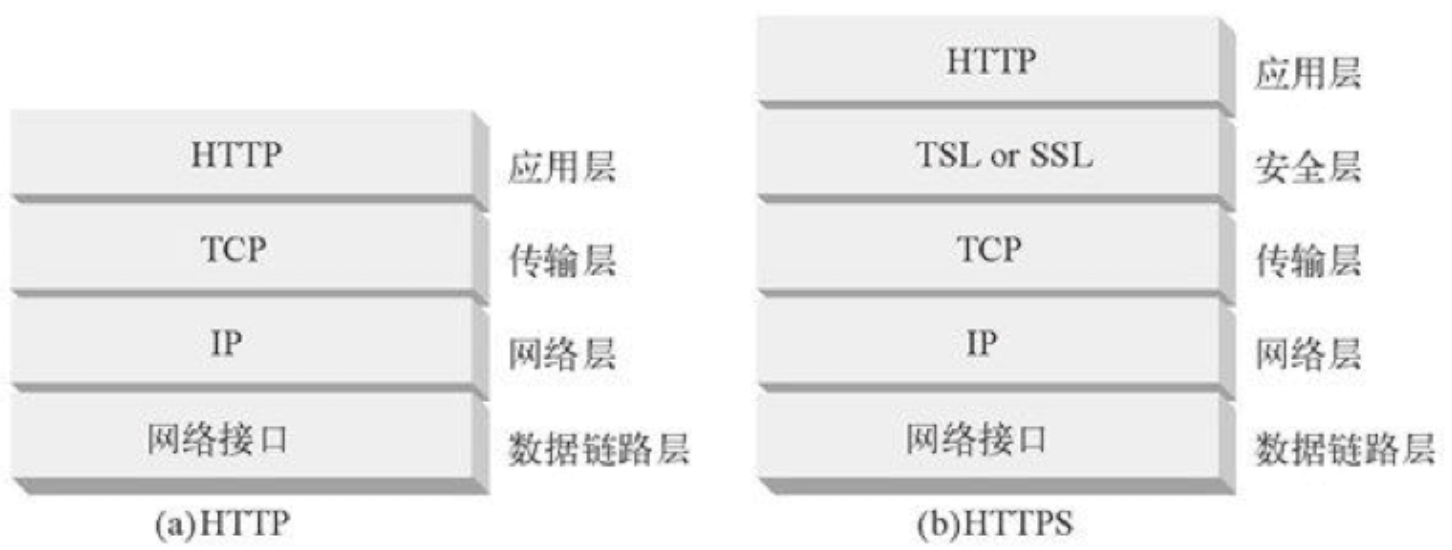
TLS粗略地又可以划分为两层:
(1)靠近应用层的握手协议TLS Handshaking Protocols
(2)靠近TCP的记录层协议TLS Record Protocol
TLS握手协议TLS Handshaking Protocols还能细分为5个子协议:
(1)change_cipher_spec (在TLS 1.3中这个协议已经删除,为了兼容TLS老版本,可能还会存在)
(2)alert
(3)handshake
(4)application_data
(5)heartbeat(这个是TLS 1.3新加的,TLS 1.3之前的版本没有这个协议)
这些子协议之间的关系可以用下图来表示:

备注:当双方通过密钥协商过程得到会话密钥后,传输的加密数据,就走到了“应用数据协议”。
TLS记录层协议
记录层将上层的信息块分段为TLSPlaintext记录,TLSPlaintext中包含2^14字节或更少字节块的数据。
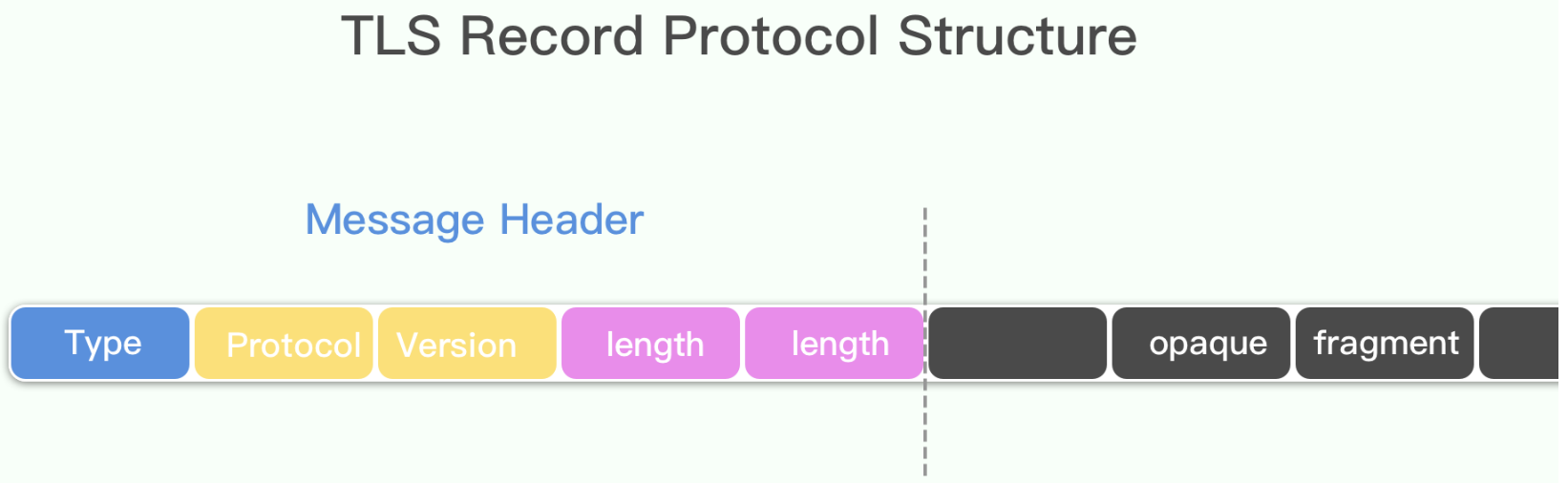
备注:上图中Protocol Version是一个字段,占2个字节;length length也是一个字段,占两个字段。相关结构体如下:
1 | enum { |
opaque fragment应该指的就是change_cipher_spec,handshake,application_data以及alert等这些子协议的内容了。
TLS密码切换协议
change_cipher_spec(以下简称CCS协议) 协议,是TLS记录层对应用数据是否进行加密的分界线。客户端或者服务端一旦收到对端发来的CCS协议,就表明接下来传输数据过程中可以对应用数据协议进行加密了。
经过TLS记录层包装以后(也就是说下面的结构是TLS记录层的完整结构,下面的Message Header头也是TLS记录层的协议头。然后后面的其他子协议都是一样的哦),结构如下:

TLS密码切换协议数据结构如下:
1 | struct { |
TLS警告协议
经过TLS记录层包装以后,结构如下:
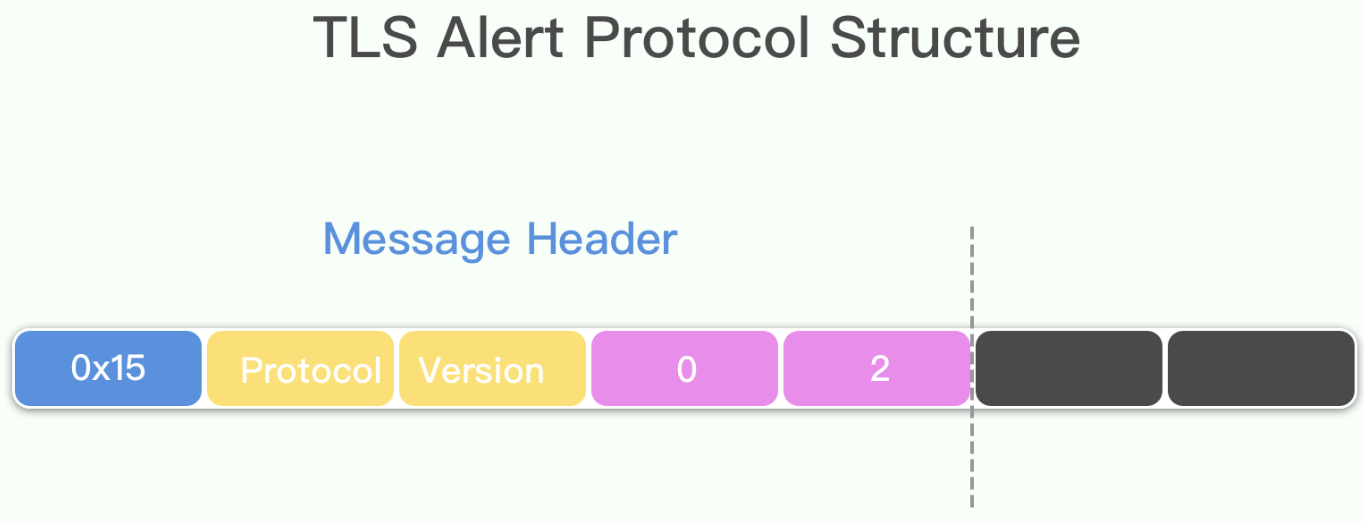
TLS警告协议数据结构如下:
1 | enum { |
TLS 1.2的所有警告描述信息如下:
1 | enum { |
TLS 1.3的所有警告描述信息如下:
1 | enum { |
TLS握手协议
握手协议是整个TLS协议簇中最最核心的协议,HTTPS能保证安全也是因为它的功劳。经过TLS记录层包装以后,结构如下:
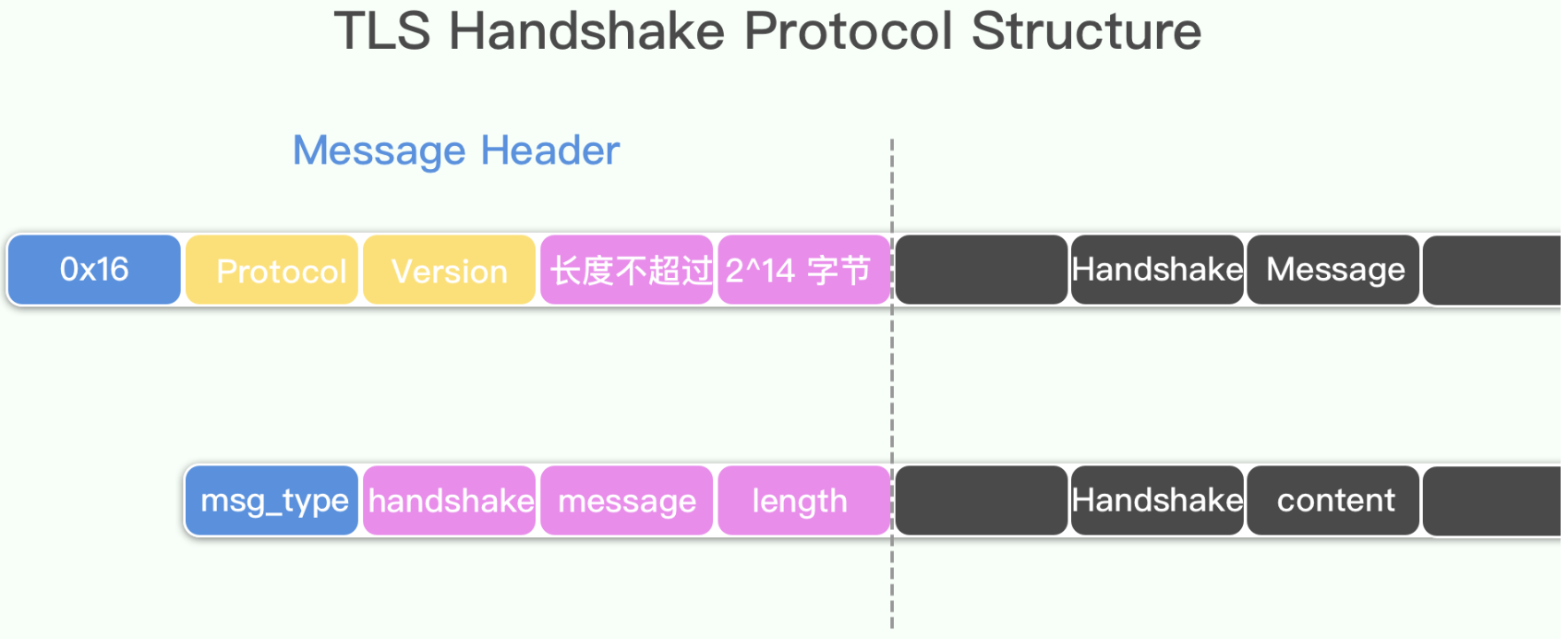
TLS 1.2握手协议数据结构如下:
1 | enum { |
TLS 1.3协议数据结构如下:
1 | enum { |
TLS应用数据协议
应用数据协议就是TLS上层的各种协议,TLS主要保护的数据就是应用数据协议的数据。经过TLS记录层包装以后,结构如下:
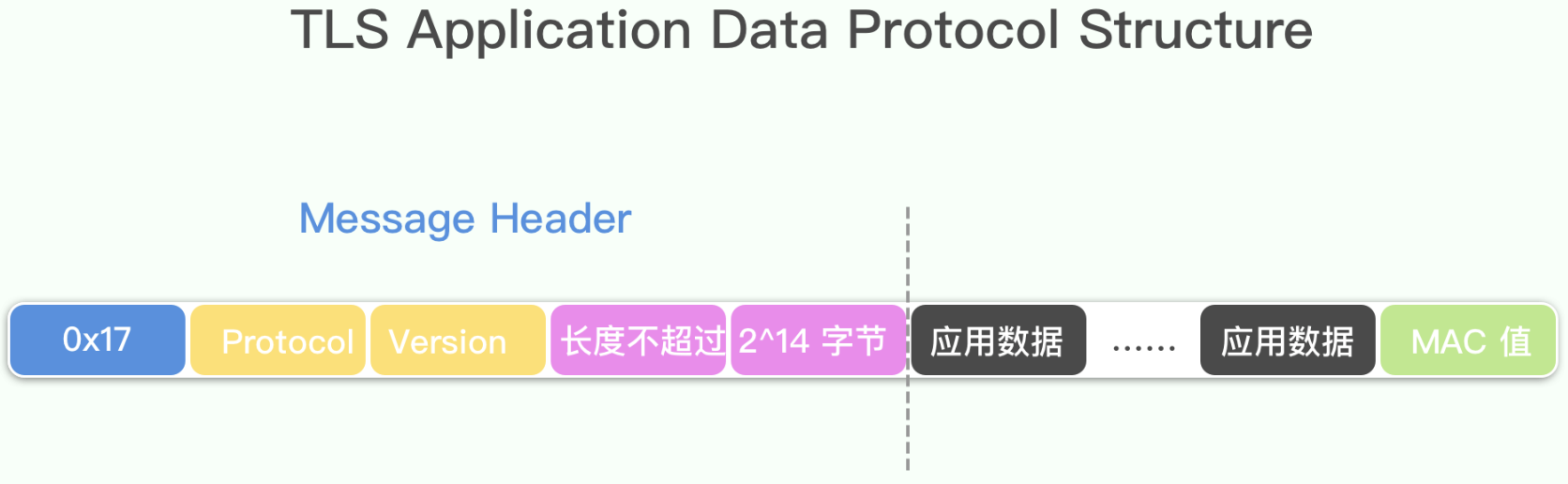
TLS心跳协议
经过TLS记录层包装以后,结构如下:
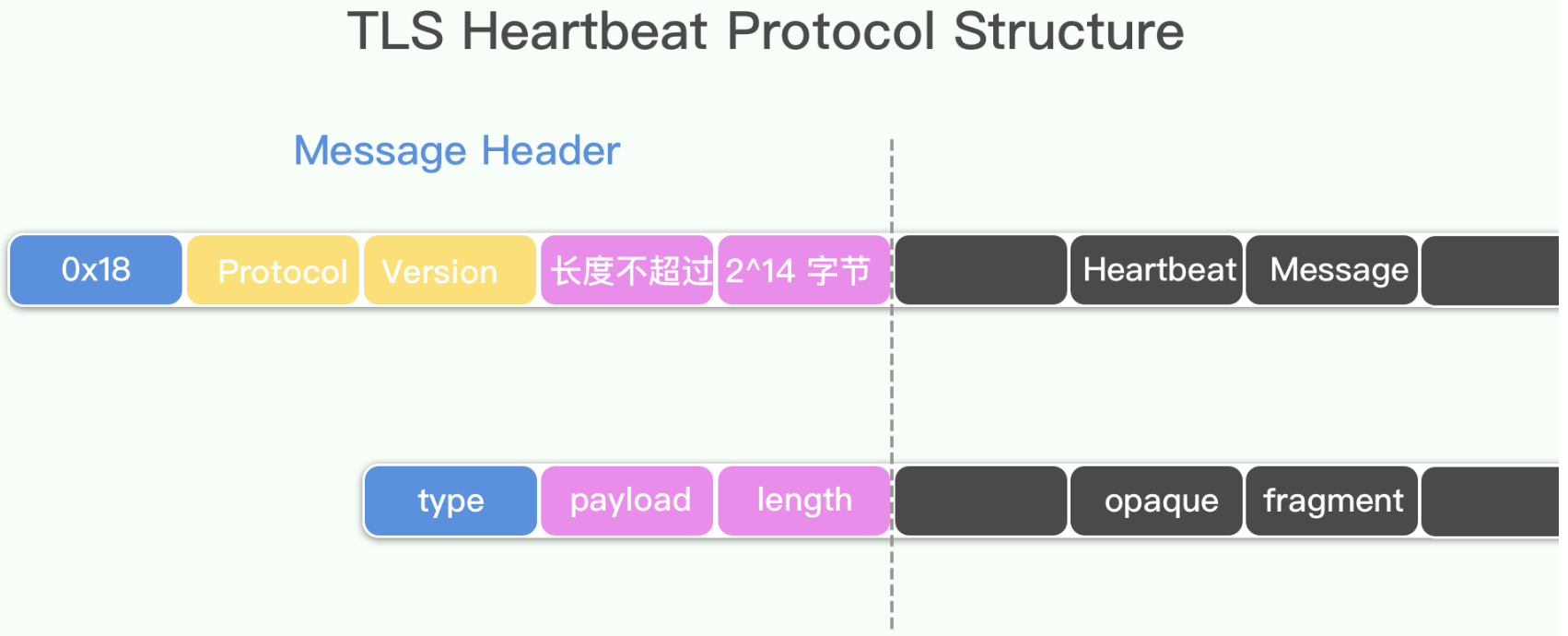
协议数据结构如下:
1 | enum { |
其他闲杂知识
(1)一个TCP包中可以包含多个TLS报文